When a new computer arrives, you (and anyone else for that matter) can install and run any applications that you like.
You’re free as a bird.
But in business, freedom can come with a hefty price. Because so long as you can install and run any software, so can hackers.
This is where Application Control comes in.
But what is Application Control, and what are the benefits?
What is Application Control?
Application Control is a piece of software that is typically installed on every device in your business. From desktops and laptops to servers (even those in the cloud), ideally every asset has Application Control installed.
Once installed, Application Control blocks the installation and operation of any applications on any device. It can also be used to limit the way that apps connect to each other, and the internet – more on that later.
If bad actors gain access to a device – or even if an employee manages to download a virus or malware – it’s impossible for malicious software to run.
That’s the power of Application Control.
But wait… if everything is blocked, how do employees do their work?
With some clever controls, you can choose the applications that are required by each employee (or group of employees), based on the nature of their role.
For example, you might create a rule that allows staff in the Sales Team to use Salesforce, but no one else.
These controls are called ‘Whitelisting‘ and ‘Ringfencing‘.
How does Whitelisting and Ringfencing work?
Whitelisting and Ringfencing can be thought of as two different types of rules that you can set for each application. Again, these can be customised for each user, or group of users.

Application Whitelisting allows you to create rules that determine which applications are trusted (approved by you) to run on each device.
For example, since all applications are blocked by default, you might use Whitelisting to allow Microsoft Word to operate.
Then, with Application Ringfencing, you can limit the way that these applications share information between themselves and the internet.
This prevents them from performing unnecessary actions and being weaponised against you!.
Back to our example, Ringfencing could be used to prevent Microsoft Word from connecting to the internet, except for Microsoft’s services. This would be critical, since Microsoft Word is often hijacked by bad actors to download malicious viruses and ransomware to target computers.
How is Application Control Managed?
So, with Application Control in place, your staff will be operating within a tightly managed environment (an obvious benefit of Application Control, more on this later). “But doesn’t that mean that well-intended people could be prevented from doing their jobs?”
The short answer is “possibly“. In order to truly unlock the benefits of Application Control, you put some streamlined workflows and people in place.
Whenever staff need to install or run an application that isn’t permitted, they can make a request (usually to your IT team) to have their application unlocked.
Requests should be escalated to nominated ‘approvers’ in your business who review each request and only permit those that are absolutely necessary.
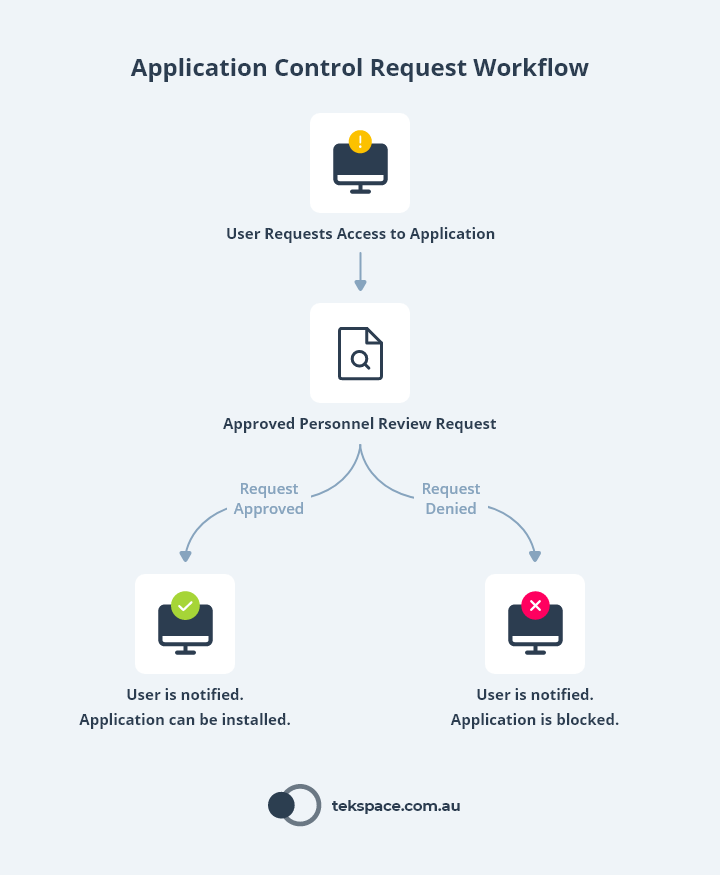
This approach gives you control over your IT environment. And for businesses who want to outsource this workflow, we’ve built a Managed Application Control service to help.
What are the benefits of Application Control?
Benefit #1: Create a ‘Zero Trust’ IT Environment
Zero Trust is an approach to cyber security that eliminates all access to and control over your IT systems or data, unless explicitly required.
Application Control is at the heart of Zero Trust, because it denies any applications from being installed or operating by default.
In other words, your data and applications can only be accessed when explicit rules and controls are activated.
Zero Trust is so powerful, that even the US Department of Defence released their own ‘Zero Trust Strategy’. No doubt, Application Control will become a key part of it’s practical implementation.
Benefit #2: Identify Current Applications
Do you really know every application that’s running in your business right now?
Probably not.
And that’s a problem, because not all software is well-intended, let alone secure.
When you first deploy Application Control, you get a birds’ eye view of every application installed in your IT environment.
It might sound daunting, but this level of insight is a crucial step to taking control of your IT and cutting out the noise.
Benefit #3: Enhanced Productivity
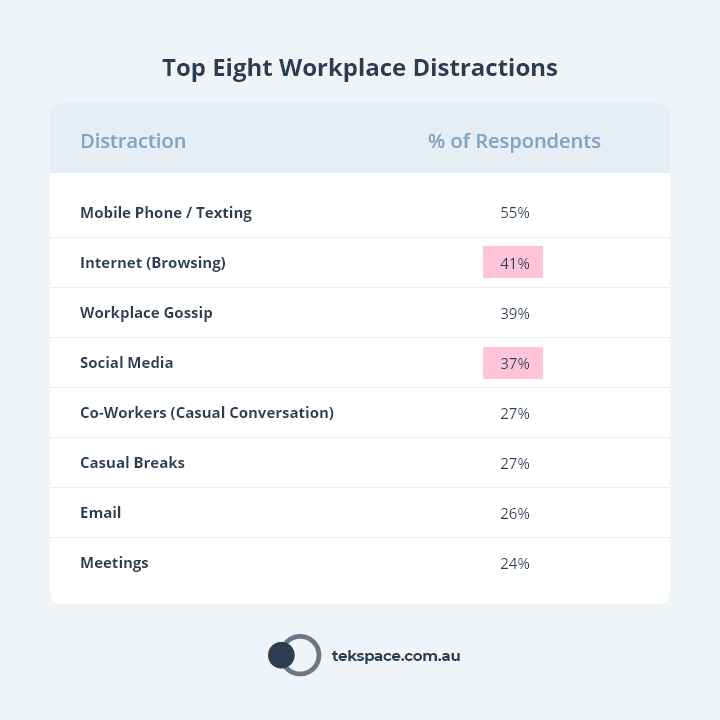
In 2016, CareerBuilder did a ‘workplace productivity’ survey of 2,186 hiring managers and 3,031 full time workers. Key findings:
- 75% of employers said that two or more hours per day are lost in productivity, because employees are distracted.
- 41% of respondents said they were distracted by the internet.
- 37% of respondents said they were distracted by social media.
Once more, Application Control could be your saving grace when it comes to employee productivity.
How? By preventing employees from wasting time on non-work related activities.
For example, if you blacklist social media applications, employees will be unable waste time on Facebook or Twitter during work hours.
Now your organisation has that time back for more productive activities.
Benefit #4: Reduced IT costs
Another benefit of Application Control is that it can help to reduce IT costs. By preventing unauthorised applications from running on devices, you can reduce the need for unnecessary IT support and maintenance. Here’s how:
- Support: With Application Control in place, staff won’t be reaching out to the support team for help with applications that aren’t core to their roles.
- Maintenance: Since there are less applications installed across your IT environment, your IT team will only need to focus their proactive maintenance efforts (e.g.: software updates) on a small group of essential programs.
But that’s not all.
By preventing unauthorised access to your organisation’s data, you’re also significantly limiting the risk of data breaches, and therefore, their associated costs.
Benefit #5: Compliance with the Essential Eight
The Australian Government describes Application Control as “one of the most effective mitigation strategies in ensuring the security of systems“. As such, it has made Application Control part of the Essential Eight.
The Essential Eight is a collection of the most important ‘mitigation strategies’ (security recommendations) that the Australian Government has recommended for all organisations. Compliance to the Essential Eight is measured according to your organisation’s ‘Maturity Level’ for each mitigation strategy (such as Application Control). Maturity Level is measured from zero to three, and generally speaking, the higher the Maturity Level, the better protected your organisation is against cyber attack.
Any organisation can self-assess their compliance to the Essential Eight, but it does require a specialised technical skillset – and sometimes, it’s better to get an outside perspective. For this reason, Tekspace offers Essential Eight Assessments.
Benefit #6: Get your internet bandwidth back
One of the hidden benefits of Application Control is the ability to reclaim wasted internet bandwidth.
In Australia, the typical city office has an internet connection with a download speed of 1000MB/s.
According to the ACCC’s “Measuring Broadband in Australia” report (August 2022), download speeds like this could enable staff to watch 14x Ultra HD or 24 HD YouTube videos at the same time.
But YouTube isn’t the only culprit. Staff can also access services like Spotify (for music), Netflix and Amazon Prime for video.
Application Control puts an end to all of that, because you can block these services at work, and get that bandwidth back!
Conclusion
Application Control is a powerful security measure that offers many benefits for organisations of all sizes. With Application Control in place, you can not only improve your security posture, but also enhance productivity, reduce IT costs and achieve compliance with the Essential Eight.
If you’d like to learn more, or discuss how Application Control can be implemented for your business, please get in touch today.

