Phishing a dangerous threat, and if your business isn’t protected, you could be at risk.
In this post, we’ll discuss what phishing is, how it works, and how you can protect your business from these attacks.
We’ll also provide some tips for preventing employees from falling victim to phishing scams. So don’t wait – read on to learn more about the dangers of phishing and how to stay safe!
What is phishing?
Phishing is an illusive form of online fraud where cybercriminals send malicious emails that appear to be from legitimate organisations (or individuals, this is known as “spear phishing”).
The ultimate goal of these criminals is to steal sensitive information, such as usernames, passwords, bank account details, credit card numbers and even your business’ intellectual property.
Armed with data like this, criminals can either steal money directly or hold the data as ransom in exchange for a payment. This is otherwise known as ‘ransomware’.
How does phishing work?
Phishing emails usually aim to convince people to click malicious links, or download an attachment. They’re typically written with a tone of urgency, such as a warning that your account has been compromised, or an offer too good to pass up.
Link-based Phishing
Link-based Phishing is when a threat actor sends a malicious email containing links to websites that host viruses, malware or attempt to steal the credentials of the target user.
These emails and links often appear authentic. For example, they could link to a fake banking website or online store.
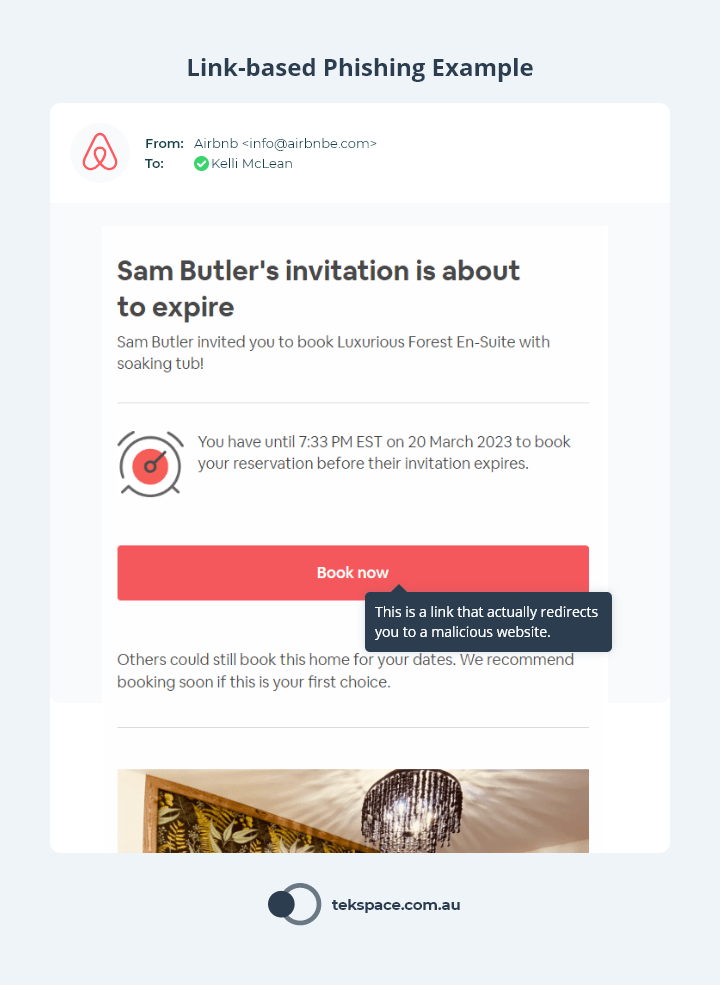
When the user clicks the link, they are taken to a website that directs them to download a (malicious) file, enter their personal information or username and password – which are then stolen.
No matter the mechanism behind link-based phishing, the intent of the hacker is always to extract the maximum value from an individual. This could be access to their bank account, their employer’s network, or both.
Attachment-based Phishing
Attachment-based Phishing leverages malicious emails to compromise a user (much like Link-based phishing).
But rather than persuading the user to click a link, they are influenced to download an attachment.
The attachment itself will often appear harmless – a common MS Word or PDF file. But in reality, the attachment is a launchpad for something far more sinister. The moment the attachment is downloaded and opened, the file will download and install malware.
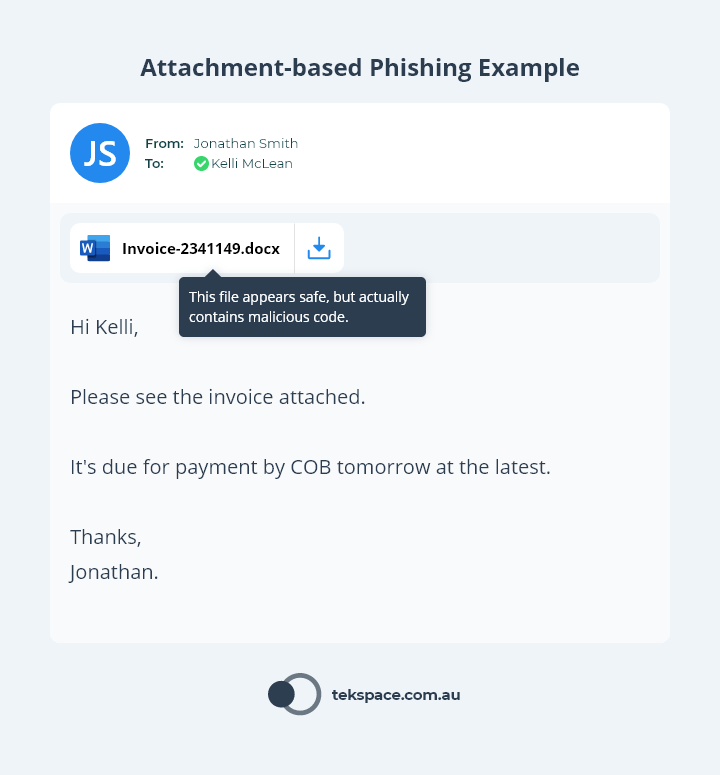
This malware gives hackers access to your corporate network, which enables them to steal data, user credentials or attack your systems.
How dangerous is phishing?
According to the Office of the Australian Information Commissioner (OAIC), phishing is one of the leading causes of data breaches. In fact, Phishing was the cause of 26% of all data breaches that were reported to the OAIC in the first half of 2022.
The consequences of a data breach in Australia are severe – both for the business that has been breached, and the customers whose data has been exposed.
But what’s at stake if you have a data breach caused by phishing? As you’ll soon learn, the dangers of phishing are only one breach away.
1. The reputational damage of a data breach
How dangerous is phishing? A data breach resulting from phishing could seriously harm your brand and reputation.
Under the Notifiable Data Breach (NDB) scheme, any organisation that is covered by the Privacy Act must notify the OAIC and any affected individuals when a data breach is likely to result in serious harm to those who have been affected.
The moment you notify individuals of the breach, the news of the data breach will be in the public domain – as was the case for Optus (see the official Optus data breach notice) and Medibank (see the official Medibank data breach notice) in late 2022.
2. The financial penalties for a data breach
How dangerous is phishing? Phishing will not only cause the loss of your data and your reputation, but potentially millions of dollars in fines.
In Australia, significant penalties may be incurred for serious or repeated breaches. In fact, these penalties may increase under The Privacy Legislation Amendment (Enforcement and Other Measures) Bill 2022.
| Penalty | Individuals | Body Corporates |
|---|---|---|
| Current Penalty | $444,000 | $2.5 Million |
| Proposed Penalty | $2.22 Million | The greater of either:
|
3. The financial cost of a data breach
How dangerous is phishing? A data breach resulting from phishing could cost millions in recovery costs.
The cost of a data breach doesn’t stop at the penalties you might incur (one might argue this is just the start!).
According to IBM’s ‘Cost of a Data Breach Report 2022‘, the global average cost of a data breach is USD $4.35 Million. In Australia, the average cost of a data breach is USD $2.92 Million – the highest it’s ever been.
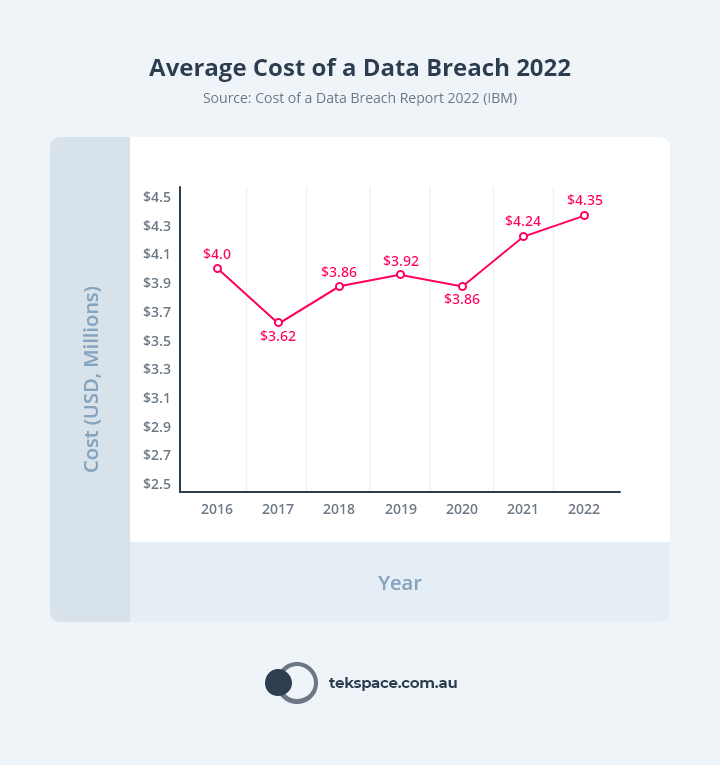
But it’s not as though organisations have one data breach, pay the price and move on.
The same study revealed that 83% of organisations have had more than one data breach.
How to protect your business against phishing
Now that we’ve touched on the dangers of phishing, let’s explore the (relatively low-cost) ways you can protect yourself.
Each of these solutions are different, but all of them – especially when added together – play a crucial role in improving your business’ cyber security posture.
Security Awareness Training
Security Awareness Training is one of the most effective ways to reduce the risk of a data breach caused by phishing.
Why? Because your people are your biggest vulnerability.
But they don’t have to be, because a solid Security Awareness Training program will convert every person in your business from a vulnerability to an active security guard.
In our Definitive Guide to Security Awareness Training, we share the secrets we’ve learned after running thousands of phishing simulations and training programs. From this experience, we’ve learned that all successful SAT programs must have the following minimum pieces in place:
- Fully Automated Phishing Simulations and Training. When SAT programs require time-consuming manual work, they are deprioritised and forgotten. Through automation, staff are more consistently engaged in the program, which gradually improves their cyber security knowledge and capability.
- AI-driven Content. As humans, we’re all different, and so are our personal vulnerabilities. Some people are more susceptible to gift-card fraud, others are susceptible to emails from HR. So when everyone receives the same content, only a small group of people receive an educational benefit. AI can massively improve the effectiveness of an SAT program by learning the unique susceptibility profile of each individual, and tailoring their experience.
- Teachable Moments: Best-in-class security awareness training platforms can not only alert users when they click on a phishing link, but also show them how they could have identified an email as suspicious.
These are just three tips, but there are many others you need to consider. Check out the guide for everything you need to know about how to deploy an effective SAT program.
Enhanced Email Security
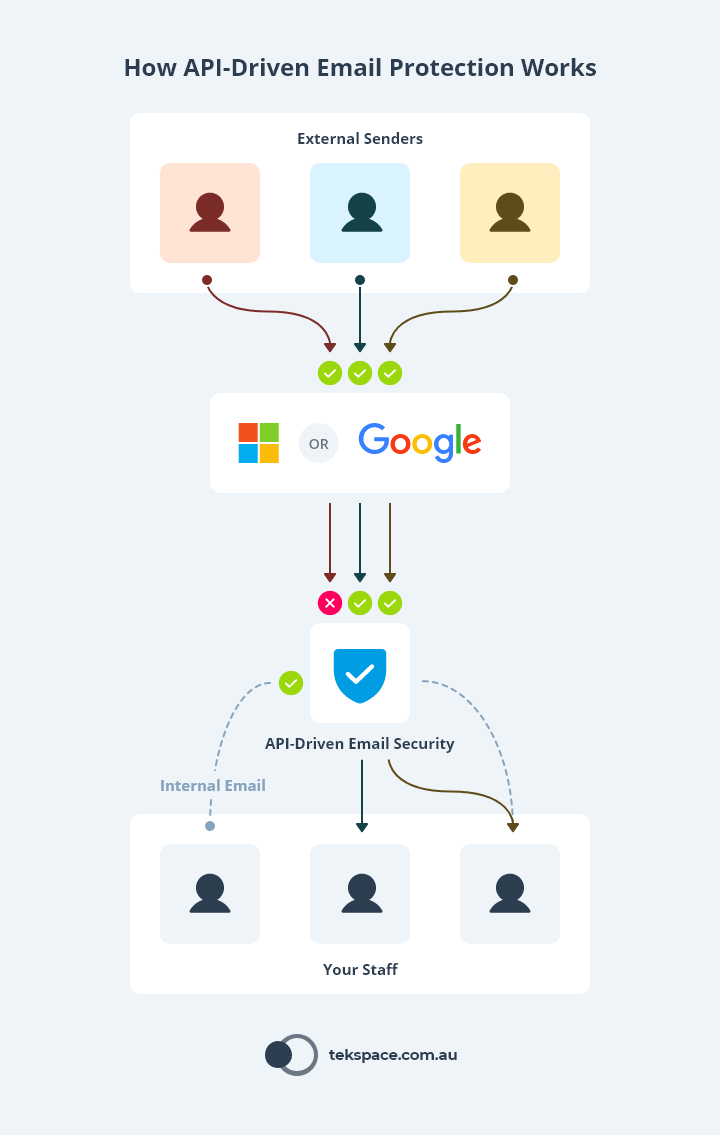
Most email platforms (such as Microsoft 365 or Google Workspace) come with email security built-in. But these solutions often fail to catch malicious emails before they reach your staff (and it only takes one…).
API-driven email security solutions are currently leading the email security space. In fact, studies show they can be nearly 10 times as effective as platform-provided solutions.
These solutions are entirely cloud-based, and are positioned behind the platform-provided email security solution.
This means that inbound emails (emails coming in from the outside) are first filtered by the platform (Microsoft or Google), then by the API-driven solution – and the reverse happens for outbound email.
But it doesn’t stop there.
Because of the way they’re positioned, API-driven email security solutions also scan emails that move internally – between your staff and systems.
Multi-factor Authentication (MFA)
Whenever you sign-in to a business system, you enter your username and a password.
In many cases, the combination of your username and password is the only piece of evidence that the business system needs to grant you access.
So when (not “if”) your username and password are stolen, hackers will use them to gain access to the system they belong to – just like you would.
As far as the business system is concerned, the correct person has been granted access because they used the correct combination of username and password.
The problem is that usernames and passwords are just text, which means:
- They can be stored and used by anyone, anywhere.
- They are static (don’t change on their own), which means they can used on a timeframe that best suits the criminal.
This is where the MFA plays a crucial role in protecting your account, your data and your business.
MFA improves security by giving the business system another piece of evidence that helps to prove the legitimacy of the user.
When the user enters their password (as they normally would) they also enter a randomly generated code, which is only valid for a few seconds. This code is supplied to the user from:
- An app on their smartphone;
- An SMS or email sent to them by the business system; or
- A small physical device that displays the code.
Unlike Security Awareness Training or Email Security, MFA doesn’t stop your staff from being phished. However, it makes it much harder for bad actors to gain access to your systems in the event that staff fall victim to phishing.
That’s why Multi-factor Authentication is one of the Essential 8 – a series of cyber security tactics recommended by the Australian Government for all businesses.
Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) is security software – like antivirus – that is installed on each of your desktops, laptops, servers and even mobile devices. These devices are called “Endpoints”. But that’s where the comparison ends, because EDR is far more powerful than Antivirus.
EDR monitors everything on every endpoint in real time. Then, using clever AI, the moment that EDR observes malicious behaviour, it locks down the threat (learn more about what EDR is and how it works).
That’s why EDR is such an important tool in the fight against phishing.
When bad actors have phished your staff and start the hunt for your data, EDR makes for a powerful last line of defence.
Conclusion
Phishing is a dangerous cybercrime and one of the leading causes of data breaches.
When hackers gain access to your business, the consequences can be disastrous – not only for the people whose data has been exposed, but for your business’ reputation and bottom line.
For these reasons, we recommend these minimum cyber security protections to keep your business safe.

