Strong Passwords
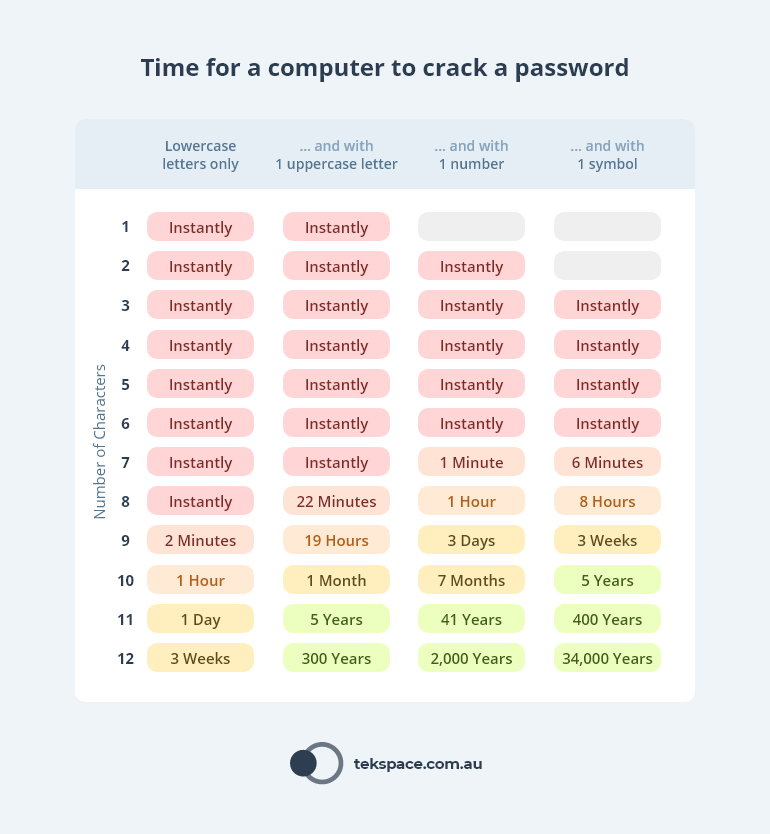
Password strength and complexity can make all the difference when it comes to securing corporate email. Data from security.org shows that even a few characters can take your password from being instantly crackable, to taking thousands of years.
Microsoft’s password recommendations are pointed at one single goal: password diversity. This email security best practice encourages the creation of unique passwords that are hard to guess. Strong passwords are those that:
- Use a minimum of 14 characters.
- Don’t require special characters (e.g.: &%!*$).
- Are not required to be reset.
- Are uncommon, and use uncommon phrases.
- Are not reused for multiple services.
Password Managers (such as Keeper) can also be implemented across your organisation to improve password (and email) security.
For your staff, these tools give them a way to create and store passwords without having to remember them. This means passwords can be far more complex, unique, and reduces the likelihood of the same password being used for more than one service.
For IT managers and executives, these tools give you a way to centralise the management of passwords across the organisation. Users can sign in to their Password Manager with SSO (which you manage) and only access the passwords that you’ve given them permissions to – often through role-based security groups.
Multi-factor Authentication (MFA)
Another email security best practice is to strengthen access controls by enforcing MFA for all email accounts.
With MFA, users must provide a second form of verification, such as a one-time code sent to their mobile device or a hardware token, to access their email.
This makes it more difficult for attackers to gain unauthorised access to a corporate email account, even if they have the user’s password.
A word to the wise, however: avoid using text messages and push notifications as forms of MFA. Text messages can be intercepted, and push notifications are often spammed by hackers until the user relents and allows them through.
Single Sign-On (SSO)
Today, the vast majority of corporate email services are held with Microsoft 365 or Google Workspace.
Both of these SaaS solutions have built-in SSO capabilities, which you can leverage as an best practice to significantly improve email security in your organisation.
SSO simplifies the user experience, reduces the number of passwords employees need to remember, and makes it easier to enforce strong access controls across multiple systems.
Account Lock-out Policies
Email accounts are often compromised through brute-force attacks. This is where a bad actor will repeatedly ‘guess’ the user’s password (usually with software) until they finally find the right combination of characters.
This approach usually means that the bad actor will incorrectly guess the password numerous times before they find the correct one.
Account lockout policies that temporarily lock accounts after a certain number of failed login attempts can be used as an email security best practice. This can help prevent brute-force attacks, where an attacker systematically attempts to guess a user’s password.
Role-based Access Control (RBAC)
RBAC is a way to grant email access permissions based on an individual’s role within your organisation.
Implementing RBAC as an email security best practice improves email security by ensuring that users only have access to the email resources necessary for their specific job functions, minimising the potential for unauthorised access or data leakage.
Get more insights like these
Receive advice from our industry-leading cyber security experts.
Tekspace will never send you spam or share your email address with a third-party.